Professional Cyber Security Services
Endpoint Protection
// An innovative solution to protect your devices
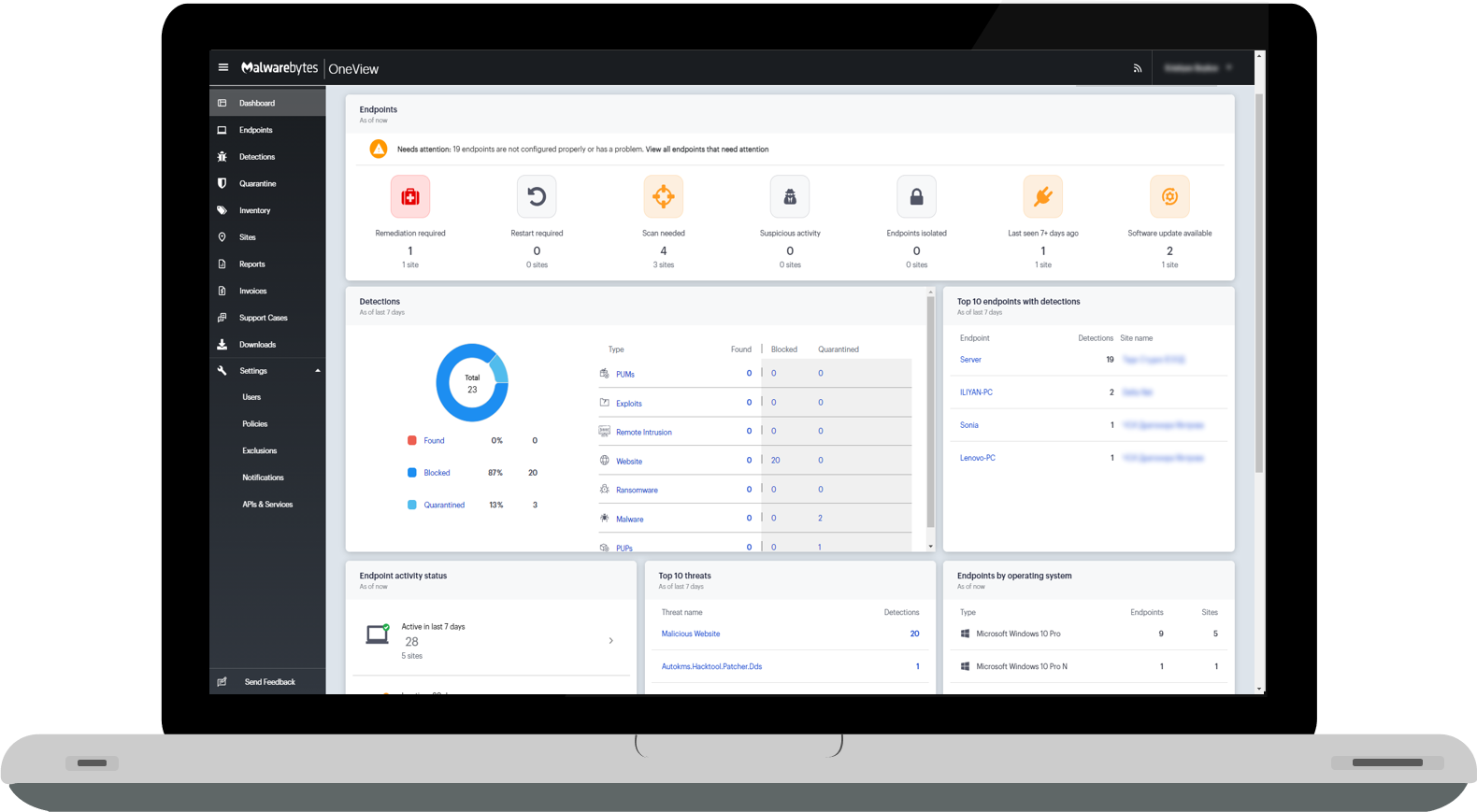
Malwarebytes Endpoint Protection
For cybercriminals, the primary target remains enterprise networks, where data, users and enterprise systems come together to generate and implement business processes. To protect your enterprise endpoints and prevent unauthorized parties from using them as entry points into your infrastructure, your IT security team should review ways to enhance your existing security. Implementing the full lifecycle of endpoint protection, from automatically blocking a common threat to quickly and appropriately responding to complex incidents, requires preventative technologies complemented by advanced defense capabilities.
Malwarebytes Endpoint Protection provides affordable security with massive visibility across all enterprise network endpoints together, with superior protection enabling the automation of routine tasks to detect, prioritize, investigate and neutralize sophisticated threats and APT-like attacks.
CYBERONE is an official partner of Malwarebytes and as such we can provide our customers with access to the Nebula® and Oneview® platforms as part of the service. Whether you use Endpoint Protection or Endpoint Protection and Response for your endpoints, we'll provide you with monitoring and support, as well as a 24/7 emergency hotline.
// Additional information about the service
Malwarebytes Endpoint Protection
Malwarebytes (EP) for Windows and Mac can easily replace or complement other endpoint security solutions, including Microsoft Defender. The software is known for being a seamless, simple and cost-effective deployment solution through a single endpoint agent and offers robust integrations and compatibility.
- Non-disruptive, deployment within minutes (even on AD networks)
- One endpoint agent, for all Malwarebytes services, simple integration
- An intuitive cloud management console that is also used by our SOC.
- Non-disruptive, deployment within minutes (even on AD networks)
- One endpoint agent, for all Malwarebytes services, simple integration
- An intuitive cloud management console that is also used by our SOC.
Enter the world of Malwarebytes Endpoint Protection, a complete malware protection and removal solution with predictive threat detection, proactive threat blocking, and integrated end-to-end protection. Powered by Malwarebytes' cloud technologies, Endpoint Protection software provides flexible management and speed of their PC and server protection software for organizations of all sizes.
With Malwarebytes cloud management software, you can easily scale to meet future requirements. Our cyber intelligence expertise provides you with a solution powered by threat intelligence from millions of endpoints, both business and consumer. Malwarebytes Nebula and OneView's REST API makes it easy to integrate with SIEM, SOAR, ITSM, etc. for further automation and compatibility.

// Advantages of our solution
Advantages and opportunities
Comprehensive protection and speed
Many endpoint security solutions flood endpoints with ever-growing databases of malware signatures, and this leads to poor performance due to heavy scanning algorithms. In contrast, Malwarebytes uses a single, low-demand agent that quickly identifies and blocks the execution of malicious code without affecting device performance.
Sophisticated web protection
The Web Protection module proactively prevents users from accessing malicious sites, malicious ads, scam networks, and suspicious URLs, as well as downloading potentially unwanted programs and those that would lead to potentially unwanted modifications. You can also add additional blacklisted or whitelisted domains, depending on your organization's policies.
The right kind of Machine learning
Instead of training for malware, Malwarebytes' Machine Learning model is trained to recognize good software - properly signed code from known vendors. The result is a predictive malware inference that becomes faster to determine and more accurate over time.
The fastest threat intelligence on the market
Take advantage of malware detection and remediation information collected from millions of enterprise and private end devices. Even new, unidentified malware is usually eliminated before it can affect your endpoints because its runtime behavior is actively monitored.
Protected devices and services
Malwarebytes secures your devices by blocking public exploits, stopping unauthorized code execution, and interrupting communication with proven malicious malware servers to dramatically reduce the risk of your organization being compromised.
Behavior-based blocking
Malwarebytes performs constant behavior-based analysis, provides near-real-time identification of behavior that is clearly malicious, and automatically blocks the threat, providing the most proactive and intelligent protection on the market today.
All Cloud management
A full suite of endpoint protection functionality and automation capabilities, managed by the Malwarebytes Nebula cloud platform and accessible from an intuitive user interface, make fighting malware a matter of clicks, not writing codes, scripts and workarounds.
Prevention of 0day attacks
Malwarebytes applies the analysis of so-called payloads that do not appear in the unified signature database and tries to find anomalies to identify and block malware that tries to exploit hidden vulnerabilities in your organization's operating systems and applications.
Tracks infection, successfully quarantines
Malwarebytes Linking Engine tracks every installation, modification, and process instantiation—including executables in memory that other anti-malware packages miss—taking a complete inventory of the threat, enabling complete remediation. Separately, the customer and security professionals have a complete history of every single change and action in the form of an intuitive interface.
Analyzes risks to save your IT team time
Our solution provides extensive threat analysis along with an assessment of their potential impact. Your IT team can save time and effectively communicate potential impacts and risks to executive management.
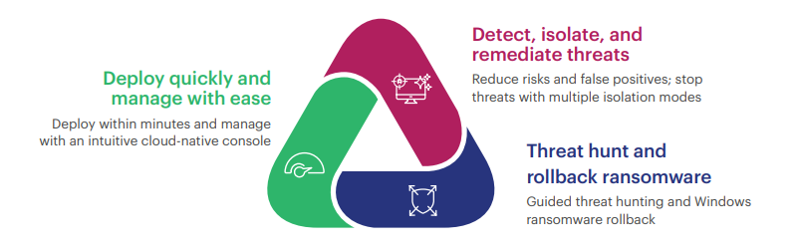
// Antivirus software solution... and more
Malwarebytes Endpoint Protection and Response
Malwarebytes EDR includes integrated endpoint protection and automated adaptive detection techniques that learn at every stage of the threat detection process. Unlike more reactive signature-based solutions that allow malware to run before it actually starts working, Malwarebytes Endpoint Protection
EDR detects and blocks threats before devices are infected. Malwarebytes EDR proactively and accurately detects and prevents both malicious code and suspicious behavior.
The software uses unique Machine Learning technology to detect not only known threats, but also to find unknown ones. Malwarebytes EDR boasts higher accuracy and lower false-positives than the normal product designed for smaller organizations, which is why they have one of the lowest false-positive rates in the industry. Granular isolation capabilities prevent lateral movement in an active attack, allowing you to quarantine and completely isolate individual machines, subnets, or groups and continue active remediation and investigation activities.
- Detects 0day threats with very few false positives.
- Granular isolation for Windows processes, networks, and desktops.
- Removes executables, artifacts, and changes to settings and registries.
- Detects 0day threats with very few false positives.
- Granular isolation for Windows processes, networks, and desktops.
- Removes executables, artifacts, and changes to settings and registries.
For Windows platforms, Malwarebytes EDR includes a unique 72-hour ransomware recovery technology that can turn back the clock and quickly return your business and its documents to a previous state. If an attack affects user files, Malwarebytes can easily roll back those changes to restore files that were encrypted, deleted, or modified in a ransomware attack.
// Advantages and disadvantages
EDR vs traditional antivirus software
On the one hand, you have out-of-the-box antivirus software designed for the user who wants to protect multiple personal devices on their home network at home. An antivirus program stops computer viruses, but it can also stop modern threats such as some ransomware, adware, and Trojan malware.
On the other hand, you have EDR for the business user protecting hundreds, potentially thousands of end devices simultaneously. The devices can be personal employee devices (BYOD) as well as workstations that are governed by the company's corporate policies.
When it comes to threat analysis, the typical user just wants to know that their devices are protected. Counting and reporting does not extend much beyond how many threats and what types of threats were blocked in a given period of time. This is not enough for a business user. Security administrators need to know “What happened to my endpoints before and what is happening to my endpoints now?” Traditional antivirus software is not good at answering these questions, but this is where EDR excels. At any given time, EDR has a view on
the daily functions of the endpoint. When something outside of normal computer operations and functions occurs, administrators are alerted, presented with the full range of incident information, and given a number of options for action.
Some capabilities that Malwarebytes EDR offers that are different from traditional antivirus software
- Isolate the computer from the network
- Isolate the user from the computer
- Shutdown, isolation and control over active processes
- Update installed software, operating system, software agent of Malwarebytes
- Possibility of full tracking of each process, what and how it performed over time, including sub-processes, impacts on other processes, etc.
- Ability to recover files affected by Ransomware in 72 hours. back.
- Ability to create detailed exceptions for files that are misdiagnosed as virus/malicious. (IP, MD5 hash, SHA1 hash, wildcard name, folder, full path exclusions)
- Ability to apply detailed policies for different software settings on protected computers.
- Ability to apply automatic notification for different events, criticality, categories, etc.
- Option to add additional threats you wish to be blocked.
Some capabilities that Malwarebytes EDR offers that are different from traditional antivirus software
- Isolate the computer from the network
- Isolate the user from the computer
- Shutdown, isolation and control over active processes
- Update installed software, operating system, software agent of Malwarebytes
- Possibility of full tracking of each process, what and how it performed over time, including sub-processes, impacts on other processes, etc.
- Ability to recover files affected by Ransomware in 72 hours. back.
- Ability to create detailed exceptions for files that are misdiagnosed as virus/malicious. (IP, MD5 hash, SHA1 hash, wildcard name, folder, full path exclusions)
- Ability to apply detailed policies for different software settings on protected computers.
- Ability to apply automatic notification for different events, criticality, categories, etc.
- Option to add additional threats you wish to be blocked.
// The free antivirus you downloaded from the internet is not enough...
Why do companies need EDR software?
The biggest threat at the moment are so-called ransomware attacks. In a really huge part of the business, it happens that even with the help of 1 compromised computer, malicious individuals access information and data for the entire company. What follows after that is usually stealing (downloading) the compromised data and infecting key company assets with Ransomware for extortion purposes.
Over the years, this practice has proven to be the MOST PROFITABLE for malicious hackers and they take advantage of it to make a quick profit. Many huge companies, some of them international giants, were extorted for millions. Some of them paid, some didn't, but most importantly, each of these companies suffered untold losses - both financial and reputational.
Organizations of all sizes are being targeted by gangs of cybercriminals looking for big results from companies that operate with valuable and/or confidential information. Local authorities, schools, hospitals and managed service providers (MSPs) are just as likely to fall victim to a hack or ransomware infection.
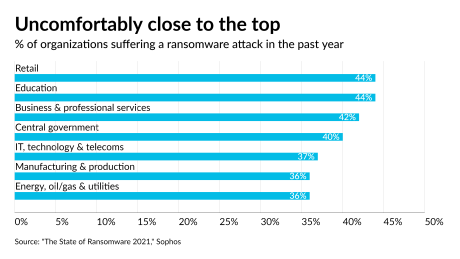
// Investing in your cyber defense is always preferable to potential losses
Benefits and return on investment
The biggest threat at the moment are so-called ransomware attacks. In a really huge part of the business, it happens that even with the help of 1 compromised computer, malicious individuals access information and data for the entire company. What follows after that is usually stealing (downloading) the compromised data and infecting key company assets with Ransomware for extortion purposes.
Incident detection
EP/EDR software solutions detect incidents that might otherwise go unnoticed. This technology proactively analyzes everything that happens on the computer to detect indicators of malicious activity. Additionally, because it collects events from all sources on the network, the system can reconstruct the timeline of an attack to help determine its nature and impact. The platform communicates recommendations to security controls – for example, changing settings or computer configuration.
Compliance with regulations
Companies use EP and EDR software to meet compliance requirements by generating reports that address all recorded security events among these sources. Without such software, the organization must manually manage all antivirus software and report/scan on demand and manually. A number of industries have mandatory security controls, some of which include the requirement for next-generation anti-virus software or centralized cybersecurity systems.
Better efficiency of the IT department
EP/EDR tools can greatly improve your efficiency when it comes to understanding and handling events in your IT environment. You can view security log data from many different hosts on your system from a single interface. This speeds up the incident handling process in several ways. First, the ability to easily see log data (logs) from the hosts in your environment. This allows your IT team to quickly identify and respond if necessary to the problem. Second, centralized data allows you to easily identify hosts that have been affected by an attack or security incident.
One solution to several problems
Companies typically use multiple different security solutions at the same time. This is due to the fact that each security solution has its flaws and shortcomings, and accordingly, with a newly identified risk, the company simply implements new software. Malwarebytes offers a cyber security solution that deals with the problems of dangerous emails, malicious domains, outdated software that allows the computer/system to be compromised, targeted attacks with popular vulnerabilities, as well as traditional Adware/Spyware problems that usually fly under the radar of most security software due to their innocuous nature.